Question:
Is it possible to connect a Clavister firewall to network equipment that runs in active-active mode and utilize both links at the same time?
Answer:
Yes, this is possible. This can be achieved with route load balancing and route monitoring. Route load balancing distributes the load to the devices that runs in active-active mode evenly and route monitor monitors the devices with ARP, ICMP or TCP and disables paths that experiences problems.
In this example we have a high availability setup that is connected to two switches or routers that runs in active-active mode. We want to distribute traffic evenly to both devices and monitor the devices at the same time. This means that both devices can process traffic simultaneously. It is necessary to have the same return paths for traffic that is load shared.
- In order to archive this we need the following:
- Allocate two separate interfaces, one for each device. If we have two switches or routers we need to allocate one physical interface for each device.
- Our primary node is located on the interface 'External_router_1'.
- Our secondary node is located on the interface 'External_router_2'.
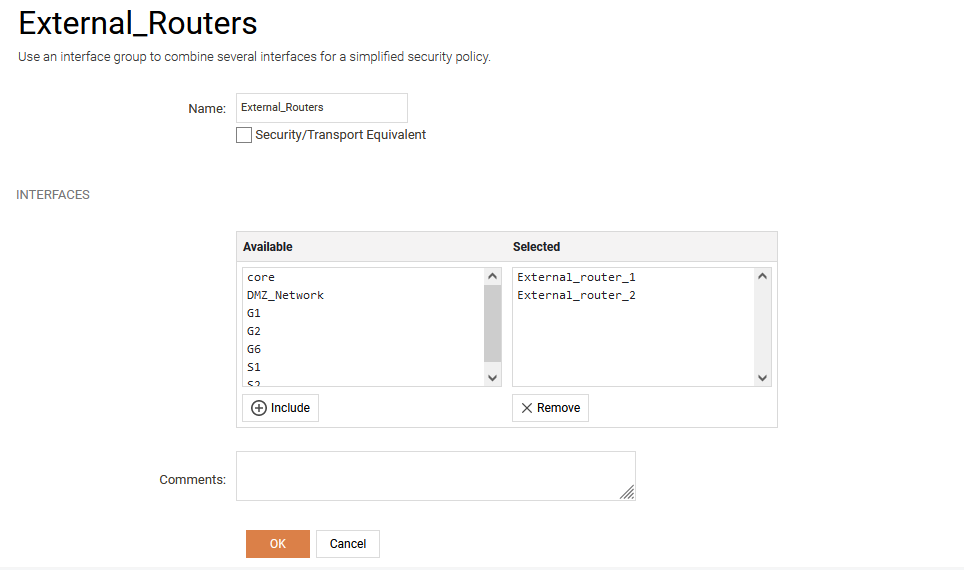
- Create an interface group that is security transport equivalent. This interface group will be used in the rule-set to allow traffic to move between the interfaces.
- Create two routes with the same metric that follows the structure:

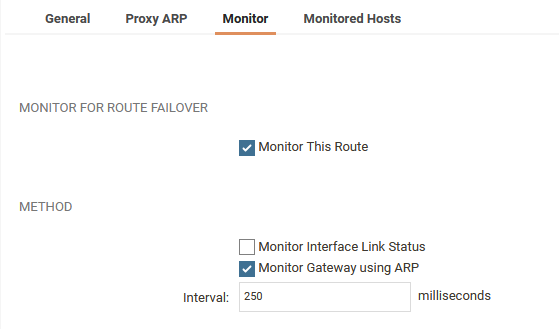
- Enable route monitoring on both routes. ARP can be used for route monitoring in this example because we want to send out ARP requests to the routers with aggressive timings. If a device is declared as down it will take less than a second to disable the path. If the device does not respond to ARP the route will be disabled.
- Goto Routing->Route load balancing and enable route load balancing on the routing table with a round robin distribution algorithm. This will distribute the load evenly over the two routes which means that the traffic will be distributed evenly to the routers or switches that runs in active-active mode because we have configured the same metric.
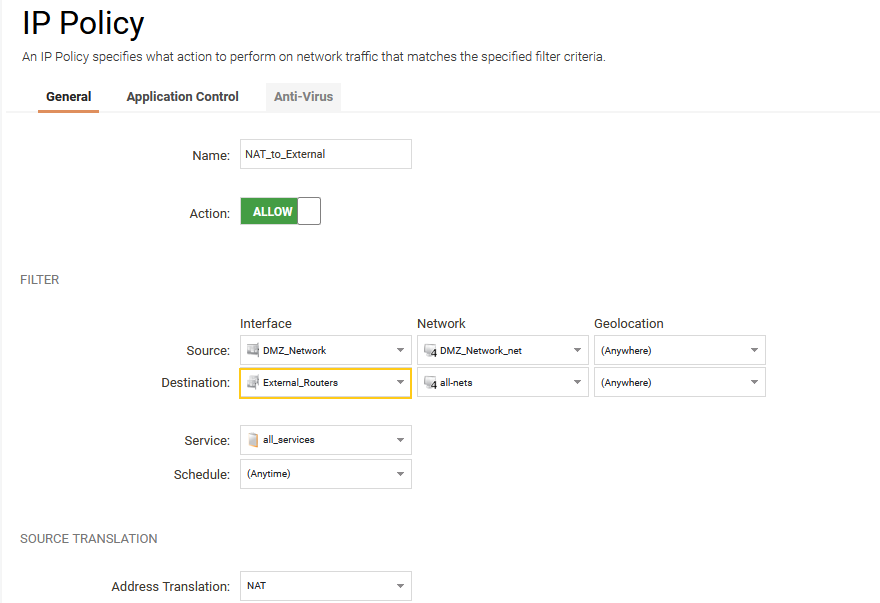
- Create an outgoing rule that allows the security gateway to send traffic to both external routers uses the interface group External_Routers as destination interface. This means that the outgoing connection is allowed to roam between External_router_1 and External_router_2 interfaces.
By following this example you will be able to connect each cluster node member to two separate switches or routers that runs in an active-active configuration and obtain redundancy and load sharing. This will be 4 paths between the equipment combined from both cluster nodes to the redundant equipment that runs in active-active mode. It is possible to combine this setup with the link monitor (System->Link Monitors) functionality that forces a fail-over between the cluster nodes if one of the links fail.
Related articles
No related articles found.