Certificate replacement instructions:
This document will show how to replace a certificate that is deployed in InControl global domain and used by firewalls as a shared object.
Firewall config:
We have an IPsec tunnel where certificate-based authentication is used. The certificate used is a shared certificate in the global domain.
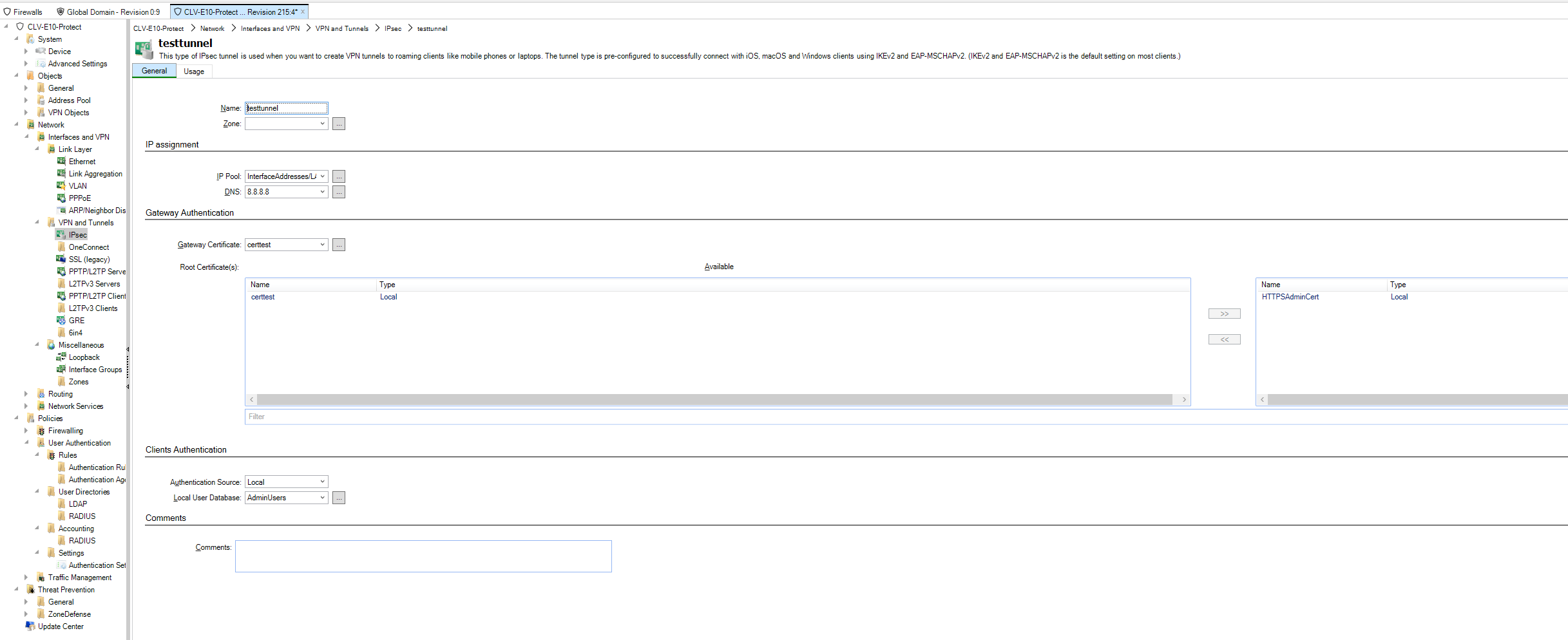
Picture A: certtest certificate from the global domain is used on configured VPN tunnel
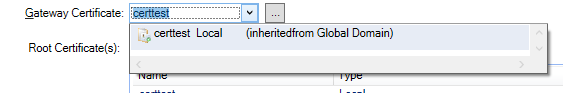
Picture B: Here we can see that it is inherited from the global domain
To update the certificate with a new one, we must configure the global domain where it is placed.
Picture C: Configure global domain.
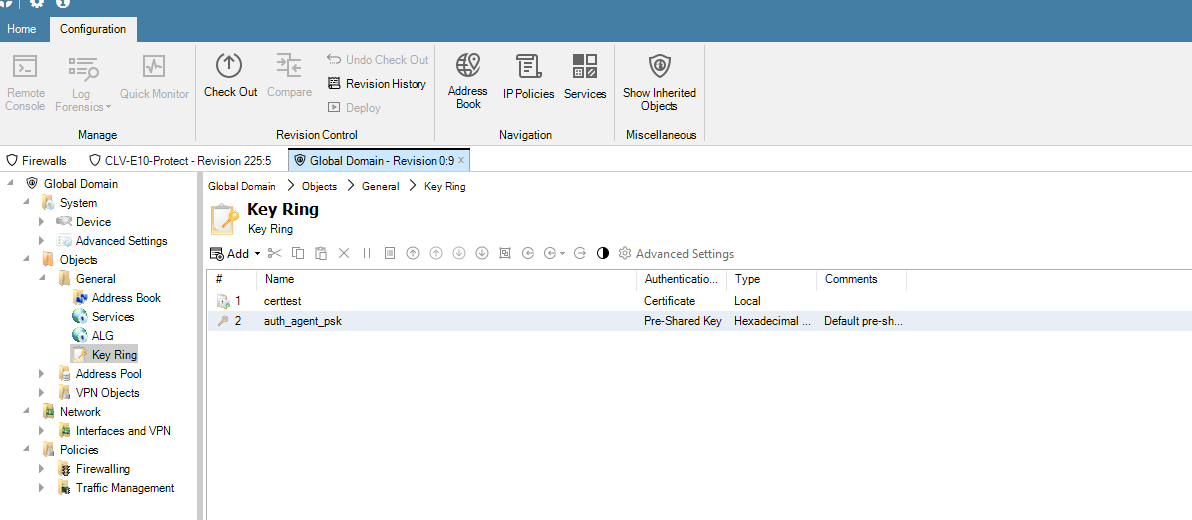
Picture D: We go to key ring where certificate is placed in global domain.
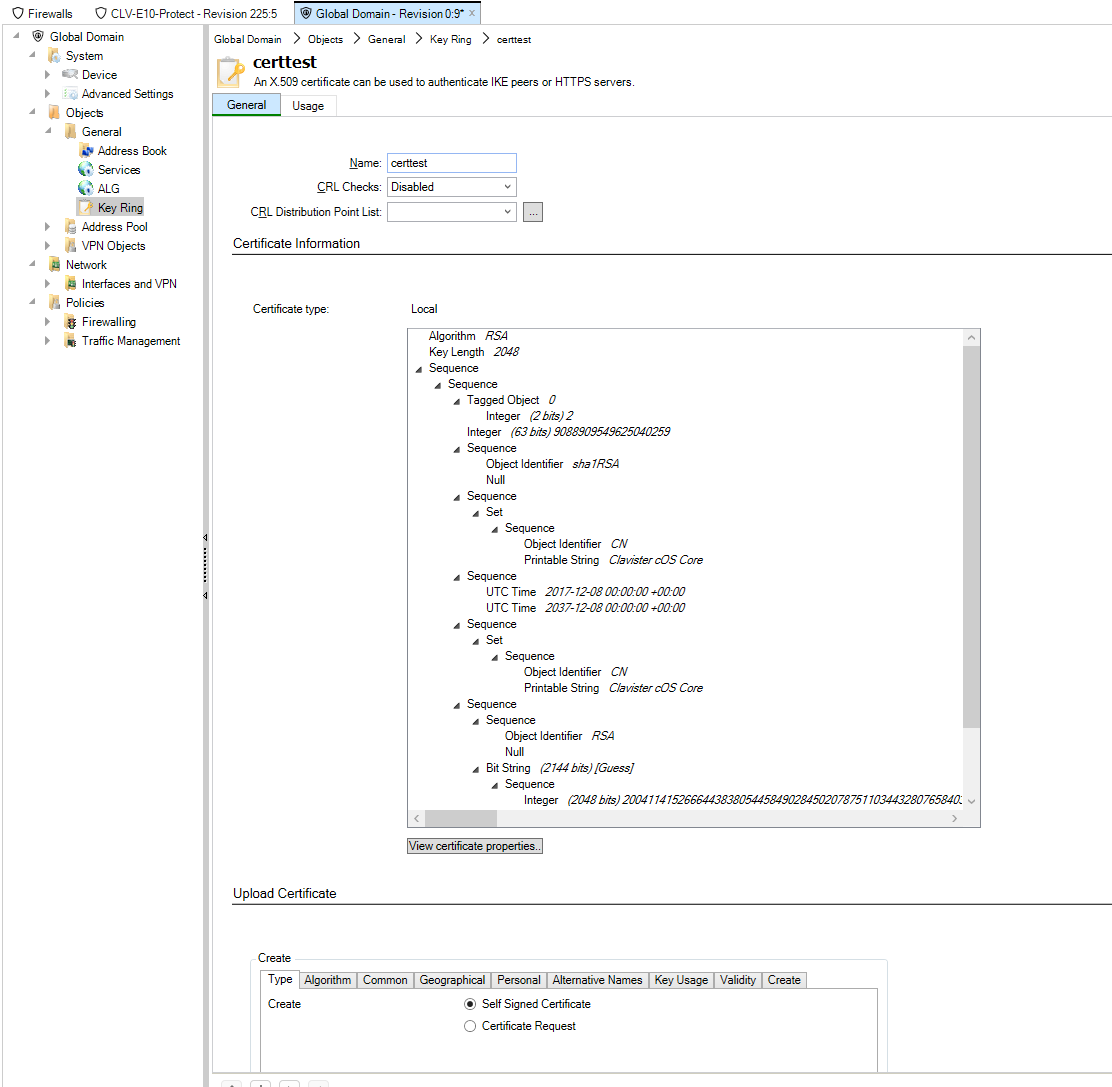
Picture E: We click on the certificate ‘certtest’ that is used on our firewalls.
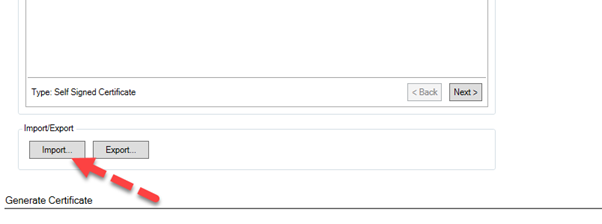
Picture F: We scroll down and click on the import button – this will import new certificates (with key if there is a private key). When import is done, InControl will ask if we want to keep old key when new certificate is imported.
We select no, because we also want to import the new key if a key exists. InControl will associate certificates and keys by name, in this example we are updating a gateway certificate where we have both a certificate file and key file, this is the naming structure used that InControl imports.

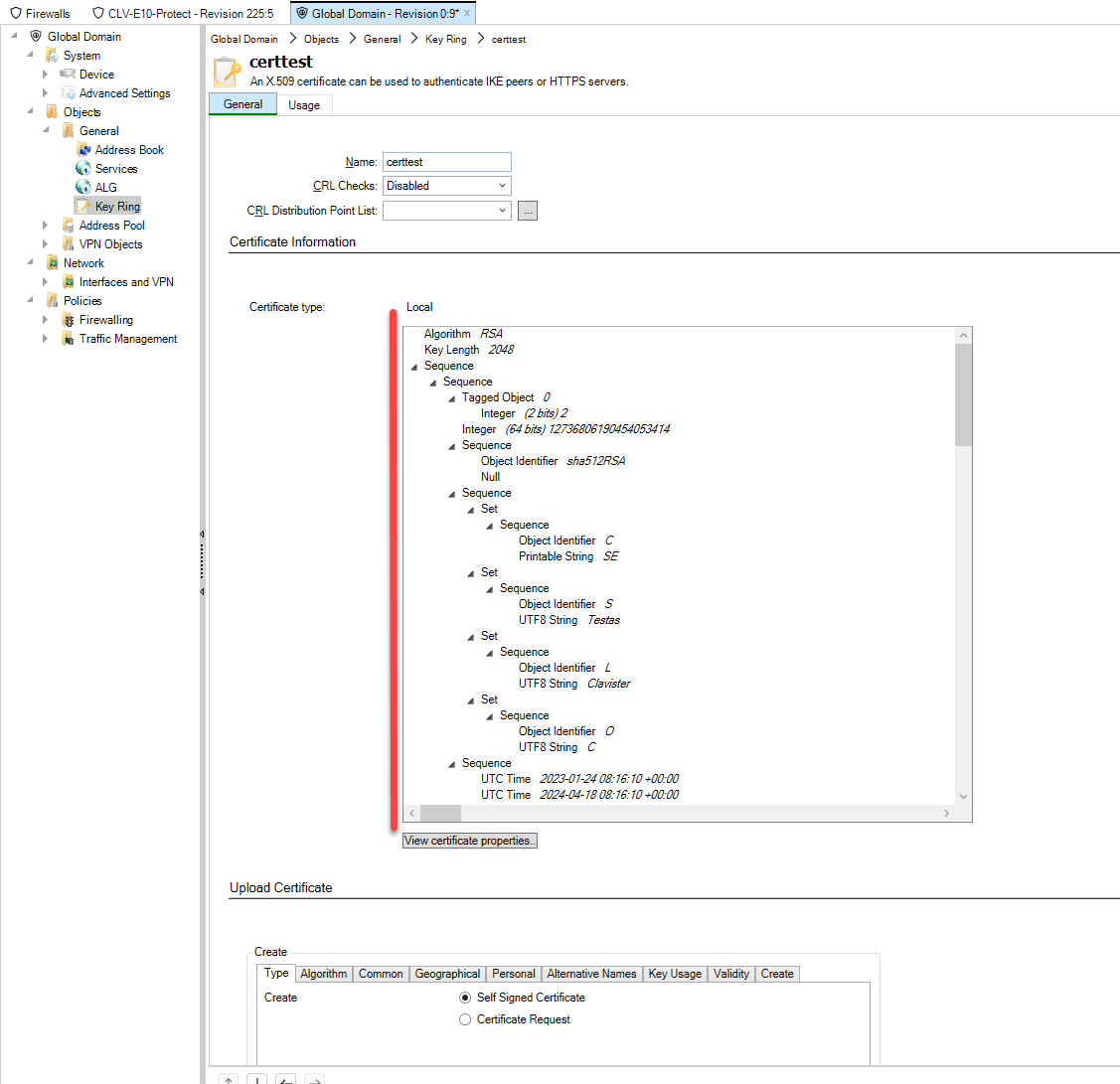
Picture G: After importing, certificate data should change. Double check that CRL setting is the same after importing.
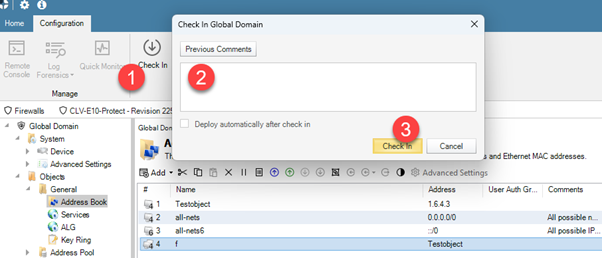
Picture H: Check in the global domain. Deploy automatically cannot be checked, deploying the changed global domain configuration to firewalls that has dependencies to changed objects is a manual action that must be done by administrator (multi-deployment is supported in this step).
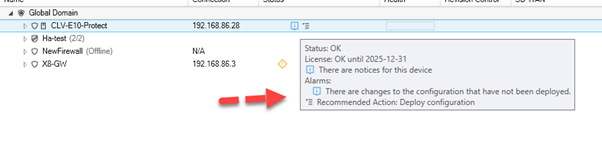
Picture I: After check in of global domain, we see that the firewall that uses ‘certtest’ for VPN tunnel, needs deployment – because the certificate has been updated in the global domain.
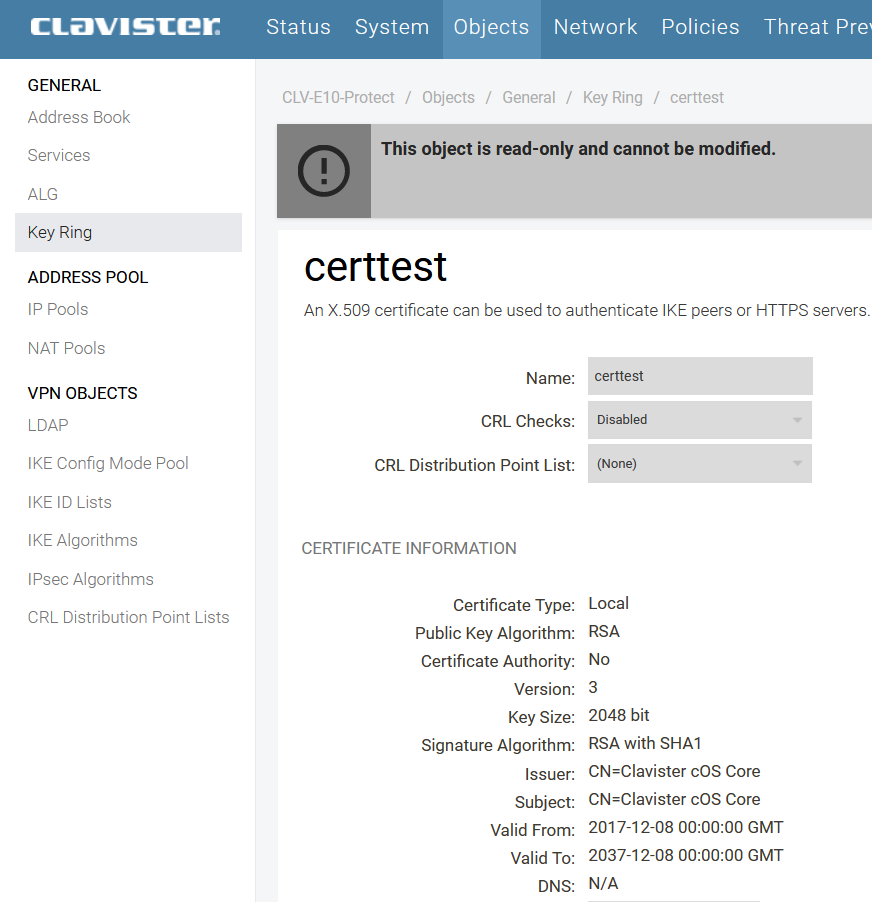
Picture J: To show very clearly what happens – we will look in the webGUI on the firewall that now uses the old certificate (before InControl deployment), then we will deploy the configuration in InControl, and the certificate content in pic J should change with content from the new certificate.
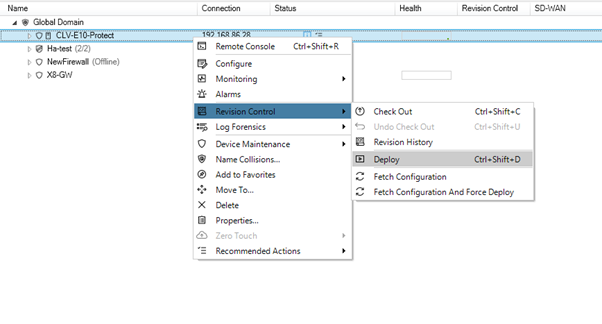
Picture K: Now we can test to deploy on one firewall In InControl before we do it on all firewalls. If something is wrong or does not work after this step – things will not work only on one firewall following this method – instead of having problems on all firewalls doing a mass deployment.
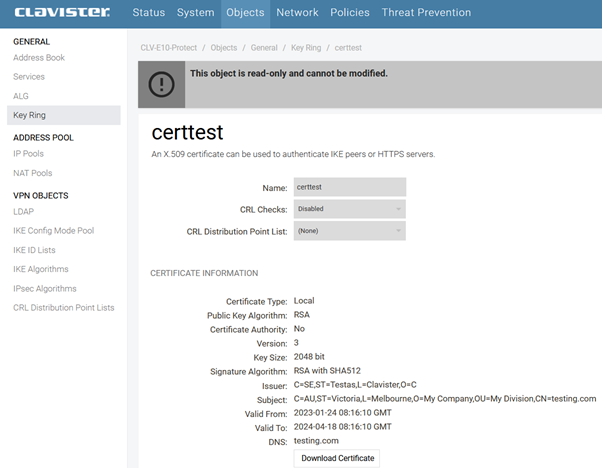
Picture L: After InControl deployment, we can see in the webGUI that certificate data has changed.
This means that the certificate change was successful.
Please check that service functionality remains after change, if it does, it is safe to deploy the certificate to more firewalls.
Related articles
11 Jan, 2023 ipsec core vpn
10 Mar, 2023 core vpn ikev2 windows radius certificate
28 Mar, 2023 ikev2 windows vpn routing splittunneling
18 Mar, 2024 core certificate oneconnect ipsec vpn
2 Feb, 2021 core sslvpn macos certificate
21 Feb, 2023 ipsec certificate windows ca core
18 Mar, 2024 onetouch sslvpn oneconnect troubleshoot certificate
20 Feb, 2023 core vpn ipsec
23 Jan, 2024 core howto certificate management letsencrypt
29 Mar, 2023 ipsec core windows vpn l2tp
16 Sep, 2020 vpn ipsec ikev2 windows howto dh
14 Mar, 2023 core ipsec vpn ikev2 certificate
11 May, 2023 oneconnect certificate howto
22 May, 2024 netwall ikev2 windows certificate vpn core