Introduction
This guide will discuss the configuration setting that excludes the default route 0.0.0.0/0 (also known as all-nets) from being exported to/from a given OSPF process running on cOS Core firewalls.
The setting will be discussed and described based on a given use case scenario.
**
Use case requirement
The network architect of company X that uses cOS Core firewall appliances, wants to dynamically advertise all the routes of a specific routing table named (Datacenter_Services_RT) within the Data center site ‘which contains 200 routes’ towards all branch sites as per the Figure-1 below:
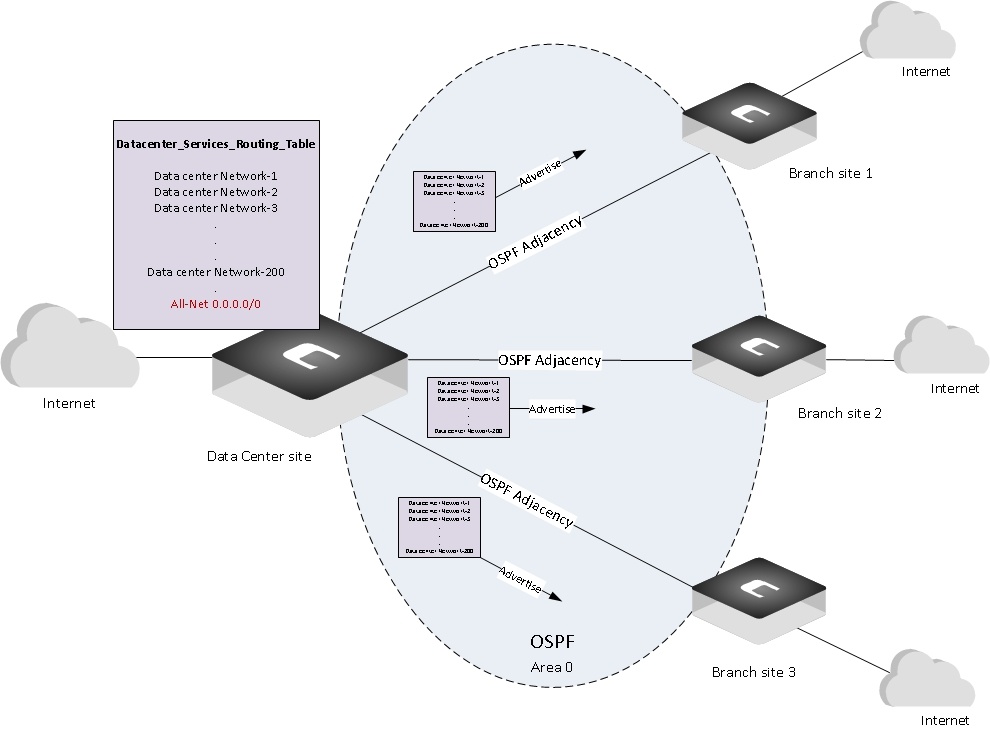
The routing requirement the architect has studied is as the following:OSPF process running on Datacenter firewall node must advertise all current and future introduced routes within datacenter’s routing table toward all OSPF neighbor processes running under Branch firewalls.
OSPF process running on Branch firewall nodes must export the learned Datacenter routes towards routing table of the branch site.
All branch firewalls must access the internet only via their respective ISP connections and not through the Data center site, hence the OSPF process under Datacenter site should NOT advertise the default route 0.0.0.0/0 towards the branch firewalls, so this default route won’t override the static default route defined under each respective branch routing table.
Solution
Since there are many routes within datacenter firewall’s routing table to be advertised by OSPF process, and the administrator would also like to advertise all future introduced datacenter routes, it is then not efficient/scalable solution to individually select network prefixes (routes) ‘within the defined routing rules’ to be exported from the routing table towards Datacenter’s OSPF process.
To address this issue, assume that there is a ‘Routing rule’ already defined under the Datacenter firewall node to catch routes from Datacenter ‘routing table’ to be exported to the OSPF process as per the Figure-2 below:
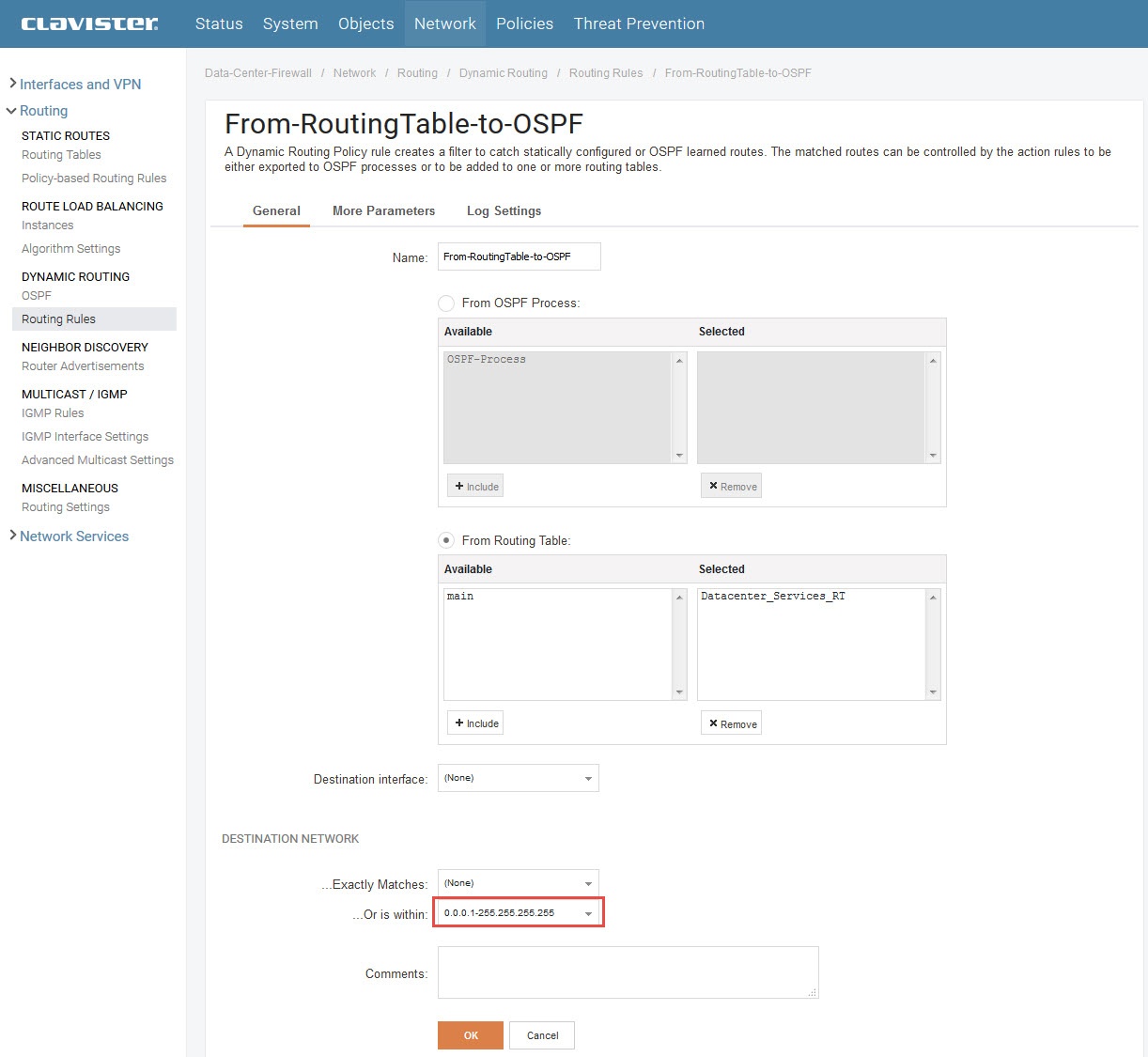
The administrator can configure the ‘…Or is within:’ setting of the defined ‘Routing rule’ with the ‘0.0.0.1-255.255.255.255’ value.
This network range value includes all possible IPv4 address values except the default route value 0.0.0.0/0. In this case, the routing rule will filter out default route ‘0.0.0.0/0’ when catching routes from Datacenter’s routing table, to be exported towards the OSPF process.
As a result, the OSPF process running under Datacenter site will advertise all routes ‘except the default route’ towards the neighbor OSPF processes running under branch sites, which fulfills the routing requirement.
Alternatively, same logic can be applied under branch firewalls instead. In this case the administrator would need to refer to the ‘Routing rule’ defined in these branch firewalls to catch routes from OSPF process to be exported towards the corresponding branch routing table and set the same network range value ‘0.0.0.1-255.255.255.255’ for the ‘…Or is within:’ setting.
Related articles
21 Oct, 2022 core arp routing
12 Apr, 2023 core proxyarp arp ipsec routing
28 Mar, 2023 ikev2 windows vpn routing splittunneling
22 Mar, 2021 core ipsec routing
11 Dec, 2025 core routing ospf ipsec
17 Jun, 2021 core ipsec routing
30 Nov, 2022 core routing
1 Jun, 2022 core routing management
25 Nov, 2022 core routing bgp
25 Sep, 2025 core routing pbr
16 Oct, 2023 howto core pbr routing netwall isp
12 Jan, 2026 core howto routing redundancy
7 Nov, 2022 core arp log routing
6 Apr, 2023 core ripv2 routing
17 Mar, 2023 core routing rules ping icmp cli
27 Jan, 2021 core stateless routing brokenlink
13 Feb, 2023 ipsec core routing failover
18 Apr, 2023 core routing transparentmode proxyarp