Description
This article will discuss how to setup user authentication in a NetWall firewall that will validate users against a FreeRADIUS server.
What is FreeRADIUS?
FreeRADIUS is an open-source implementation of the Remote Authentication Dial-In User Service (RADIUS) protocol. RADIUS is a client/server protocol used to authenticate and authorize network access, such as for wireless or VPN connections. FreeRADIUS provides a scalable, high-performance RADIUS server that is used by many organizations to manage user authentication and authorization in their networks. It can authenticate users against various backends, such as LDAP or SQL databases, and supports a wide range of authentication methods, such as username/password, EAP-TLS, and more.
Configuring FreeRADIUS
Clavister Vendor Specific attributes
FreeRADIUS must notify cOS Core that any user that matches this policy belongs to a certain group. This is done by letting FreeRADIUS send a Vendor-Specific-Attribute (VSA) to cOS Core as a part of the remote policy.
To add the Clavister Vendor Specific attributes: (These are predefined in newer releases of FreeRADIUS, /usr/share/freeradius/dictionary.clavister)
nano /etc/freeradius/dictionary. (Edit and add the following line.)
$INCLUDE /usr/share/freeradius/dictionary.clavister
Adding a client
In order for cOS Core to be allowed to communicate with FreeRADIUS it has to be added as a client.
Nano /etc/freeradius/clients
client 192.168.2.0/24 {
secret = 123456
}
The Key is the shared secret that is used to encrypt the user-password when a RADIUS-packet is being transmitted, so the same consideration as when choosing a regular password should be taken (the password should be hard to guess, not too small, etc). Clavister cOS Core supports shared secrets up to 100 characters. Remember that the shared secret is case-sensitive.
Setting up users
Note. Auth-Type = System, This means that it will use the host OS user accounts.
nano /etc/freeradius/users
DEFAULT Auth-Type = System
Clavister-User-Group = "ADMIN",
Fall-Through = 1
When this is done, we need to restart FreeRADIUS.
In case of problems, we can start FreeRADIUS in debug mode which will provide us with more details about what is going on.
$ freeradius -X
Something like this is an example of expected output want to see:
Sending Access-Accept of id 86 to 192.168.2.39 port 4961
Clavister-User-Group = "ADMIN"
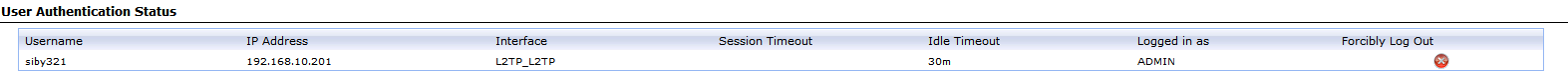
Status in the WebUI:
Example use case in cOS Core
One example of how to use FreeRADIUS can be found in the following article:
https://kb.clavister.com/324736225/roaming-ikev2-tunnel-setup-in-cos-core-with-xca-ca-and-freeradius
Please note that there are many scenarios where you can use User Authentication towards a Radius server, the above is just one example. For more information see the User Authentication section in the cOS Core admin guide located here : https://docs.clavister.com/products/netwall/
Related articles
10 Mar, 2023 core vpn ikev2 windows radius certificate
24 Apr, 2023 core legacy activedirectory radius userauth
11 Apr, 2023 ldap core authentication radius
21 Jan, 2021 easyaccess radius
24 Feb, 2021 easyaccess radius
12 Apr, 2023 howto core authenticator authentication webauth captive
4 Nov, 2024 oidc core authentication
24 Feb, 2021 easyaccess radius saml sso onetouch
21 Nov, 2025 oneconnect sase cloud radius
5 Apr, 2023 core nps ipsec radius legacy
21 Nov, 2022 radius ldap authentication core