This How-to applies to
- Clavister cOS Core
This how-to assumes that you already got the Security Gateway and the IPsec tunnel up and running.
Topics covered in this how-to
- Description of the scenario
- Setting up the routing
- Setting up the interfaces
Description of the scenario
In this scenario we have a remote office that is connected to the HQ over IPsec and we want all traffic to always go trough the IPsec tunnel for everything the inside network wants to access. Utilizing the Virtual Router support in Clavister Security Gateway makes this possible.
NOTE:
All traffic originating from the Security Gateway itself will always use <main>, that means that traffic like DNS queries, HTTP Poster, NTP and IPsec traffic will use the default gateway defined in that routing table.
Setting up the routes
First of all we need to setup the two different routing tables, <main> and <VR>
Main Routing Table
The first thing to do is to remove all routes from the routing table that has nothing to do with the external network and the Internet, i.e. the internal routes in this case.
When this is done, you should have only two routes in the <main> routing table, it should look something like this:
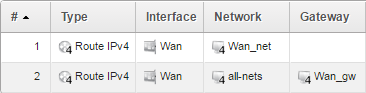
VR Routing Table
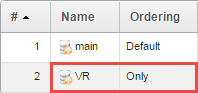
Now it’s time to create a new Routing Table, give it a name, in this How-to we will use VR and choose Only as ordering.
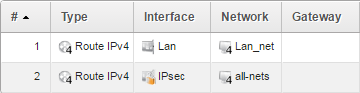
In this new routing table, add a route for the internal network and a route for all-nets over the VPN interface.
Setting up the interfaces
When the routing tables are configured the interfaces of the Security Gateway needs to be configured as members of the different routing tables. As standard all interfaces are members of all routing tables but in the scenario we want to force traffic from the VPN and inside to go only trough the <VR> routing table. This is done by defining Virtual Routing Membership on the different interfaces.
Ethernet
For the ethernet interfaces we want to configure Wan as a member of the <main> routing table and Lan in the routing table <VR>. This setting is found under the Virtual Routing tab of the interface
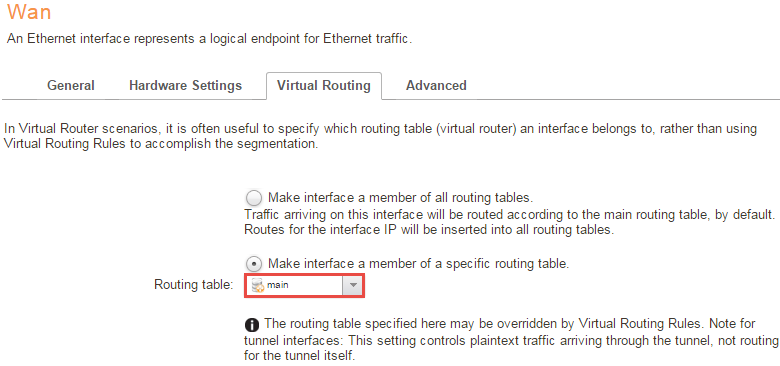
In this picture example we are using the Wan interface.
IPSec Tunnels
For the IPSec interfaces we want to configure IPsec as a member of the Routing table <VR>.
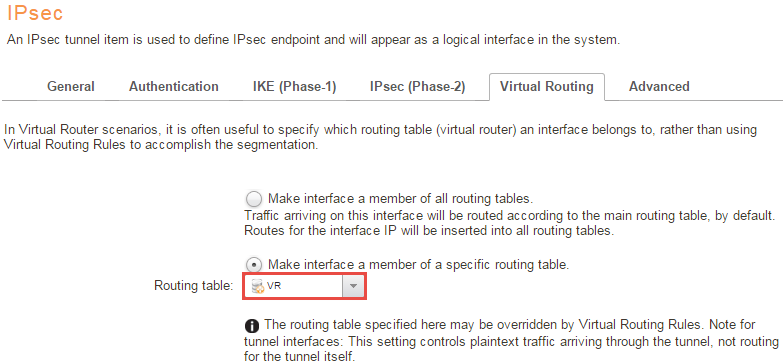
Alternative solution
It is also possible to solve this scenario without using additional routing tables, and that is by removing the default route from the <main> routing table and instead routing all-nets over the IPsec interface.
NOTE: The IPsec tunnel itself, must have all-nets defined as remote network, or traffic will not be allowed through the tunnel.
You also need to add single host routes for these addresses:
- The endpoint of the IPsec tunnel. Usually it also needs the gateway defined: RouteIPv4 Wan remotegw_ip gateway=My_ISP_gw_ip
- Hosts, such as NTP server, Clavister's CSPN servers etc that provide Antivirus updates etc, if they should not be accessed via the tunnel.
Related articles
11 Jan, 2023 ipsec core vpn
24 Mar, 2023 core ipsec ippool dhcp
12 Apr, 2023 core proxyarp arp ipsec routing
18 Mar, 2024 core certificate oneconnect ipsec vpn
5 Feb, 2021 incontrol howto backup windows
23 Nov, 2022 core ipsec
21 Feb, 2023 ipsec certificate windows ca core
22 Mar, 2021 core ipsec routing
18 Mar, 2024 core incontrol certificate oneconnect ipsec vpn
11 Dec, 2025 core routing ospf ipsec
17 Jun, 2021 core ipsec routing
8 Mar, 2023 core l2tp ipsec
12 Apr, 2023 howto core authenticator authentication webauth captive
20 Feb, 2023 core vpn ipsec
24 May, 2021 core howto mdns multicast transparentmode airprint igmp dns
26 Jan, 2022 howto incontrol installation
4 Aug, 2023 core ipsec troubleshoot ike
25 Feb, 2022 oneconnect windows howto
14 Apr, 2021 core license ipsec
8 Sep, 2020 core ipsec rules access
23 Jan, 2024 core howto certificate management letsencrypt
29 Mar, 2023 ipsec core windows vpn l2tp
5 Apr, 2023 ipsec core
28 Oct, 2020 core howto ethernet packetloss cpu
16 Sep, 2020 vpn ipsec ikev2 windows howto dh
7 Dec, 2022 ipsec ike troubleshoot core
14 Dec, 2022 core ipsec
16 Oct, 2023 howto core pbr routing netwall isp
5 Apr, 2023 core nps ipsec radius legacy
14 Mar, 2023 core ipsec vpn ikev2 certificate
12 Jan, 2026 core howto routing redundancy
23 Aug, 2022 core ipsec license memory
11 May, 2023 oneconnect certificate howto
15 Mar, 2023 core ipsec ipv6
30 Nov, 2020 howto core cloud-init dhcp
23 Aug, 2022 core connections ipsec memory
13 Feb, 2023 ipsec core routing failover
28 Mar, 2023 dhcp ipsec core