Problem
When configuring Threshold rules it blocks traffic that exceeds the configured threshold limit, but it also blocks/interrupts traffic for networks/PC’s placed in a whitelist.
Explanation
The reason for this behavior is because threshold works on a connections per second or total connection limit in order to block or hinder traffic exceeding the threshold. Once the limit has exceeded threshold can be configured to also add the source IP or network to a blacklist. And it is after adding the host/network to the blacklist that whitelist can perform an action, what whitelist can do here is that it can avoid/stop that the source IP or network is added to the blacklist but it will not stop the threshold rule to interrupt the traffic once the limits has been exceeded. So whitelist can only partially avoid interrupting traffic due to threshold trigger.
Note: An RFE (request-for-enhancement) exists towards engineering about enhancing whitelist to also stop threshold from interrupting hosts/networks placed in a whitelist, the developer ID is COP-7774.
Workaround
A workaround to the problem would be to exclude e.g. management machines from being scanned by Threshold. The easiest way to do that is to create a group object and exclude hosts we do not want to be scanned by threshold using the exclude button as shown in the below screenshot.
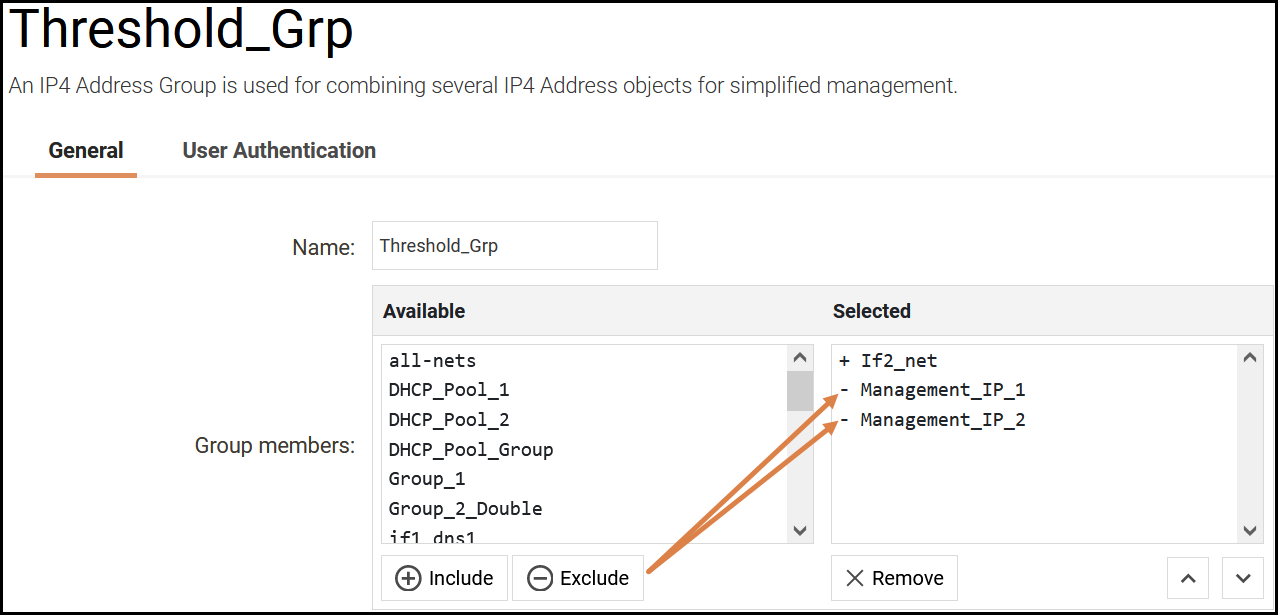
Once the object has been created, we use it in our threshold rule, effectively stopping Management_IP_1 and Management_IP_2 that is part of the “If2_net” from being scanned (and possibly interrupted) by threshold.
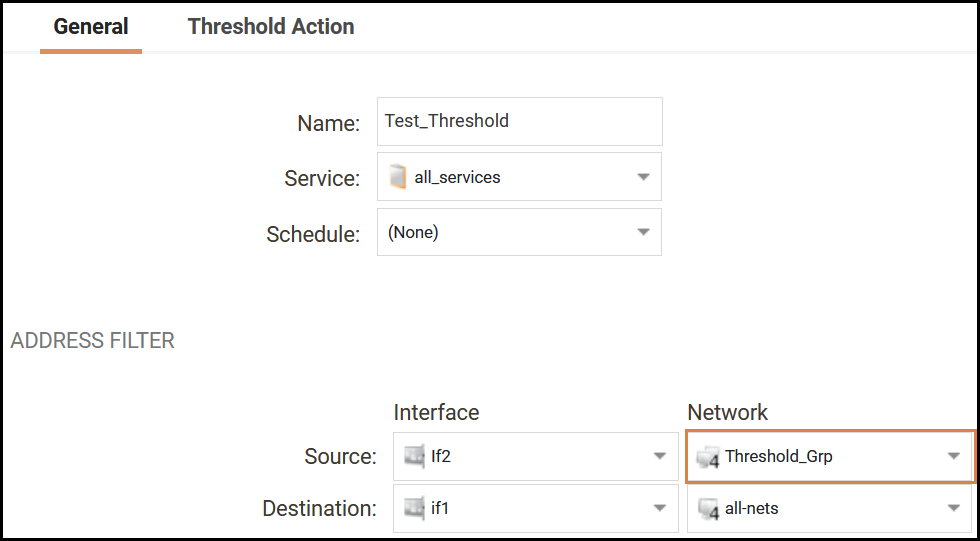
And to further clarify the network objects used in the example.
If2_Net = 192.168.10.0/24
Management_IP_1 = 192.168.10.50
Management_IP_2 = 192.168.10.51
So in the above example, all IP’s in the 192.168.10.0/24 will be scanned/monitored by threshold except IP address 192.168.10.50 and 192.168.10.51 as they are excluded from the /24 network.
Related articles
No related articles found.