Description
Configuration of user authentication related to IP Policies has been updated. Instead of configuring user authentication on the address object, a new User Group object has been introduced. This new object can be used as a filter directly on an IP Policy. During upgrade a conversion to the new format will be done. Nested objects are not possible to convert automatically.
IP Policies, IP Rules, Threshold Rules, IDP Rules and Routing Rules referring to network objects that could not be converted will be disabled after the upgrade, to let the administrator verify them before manually activating them again. Review the configuration log after the upgrade, any object that was not converted will be listed here. Disabled objects will also be logged in the console CLI during the first start up of the new version.
Example
To better describe the type of object(s) that cannot be migrated, we have the following example from a 14.00.xx configuration.
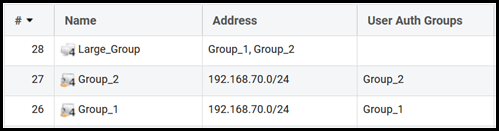
- First we have two network objects (these are not a group object, the object is simply called Group_1 and 2) in the address book that have User Auth Groups enabled, Group_1 and Group_2 as shown in the right-most column.
- These two objects are then used in a Group object called "Large_Group". Here we effectively have a nested group object that cannot be converted.
- If we now use the "Large_Group" object in e.g. an IP Policy like this:
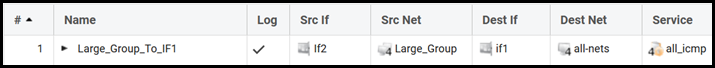
- After the upgrade, this would result in the above IP policy being disabled and manual intervention is required.
Tip: After system start-up after the migration, use the CLI command “cfglog” to save information about which objects that potentially got disabled and then go through them one-by-one. This log is reset/updated at next configuration deployment and information from the upgrade may be lost.
Recreating the User Auth Policy After the Upgrade
To re-create the IP policy to behave the same as before the upgrade, the following steps are needed.
- Create a new User Group object under Objects
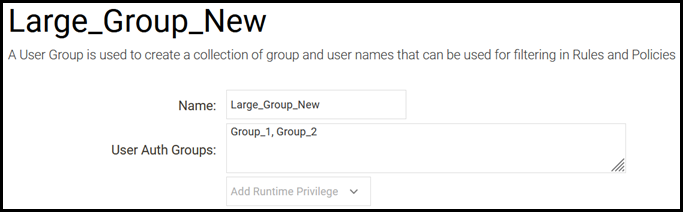
- In the new User Group object, we add Group_1 and Group_2 again. We call the new object "Large_Group_New" to avoid any confusion.
- We now use the previously created object on the new "Source User Group" under Advanced Filters as shown below.
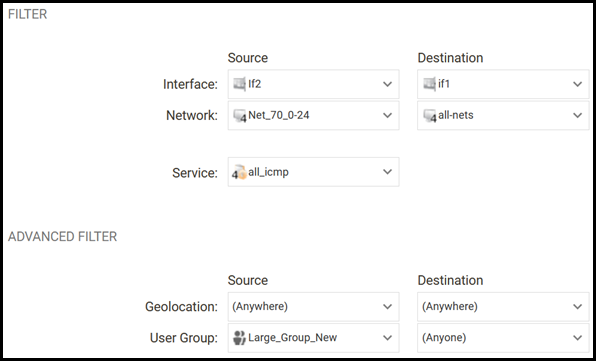
- Since User Auth objects are not set on the source network any more, we set a normal network object as the source network as shown above.
Important: Please note that the above is just an example. There are many variations of which network, user group object etc. that can be used and where. The above example may not be exact to the scenario encountered.
Related articles
17 Nov, 2022 core license updates idp antivirus wcf ipreputation applicationcontrol