Description
Lets Encrypt certificates can be used in cOS Core for example to OneConnect, IKEv2 and HTTPS Management. The certificates are however only valid for only 90 days and needs to be renewed several times per year, which might be a hassle if done manually. Can the update procedure be automated?
Scenario
A third-party reverse proxy, such as Nginx, is set up and configured. On that host, Certbot is configured to handle certificates for one or several domains. One of these certificates is configured with a domain name used by cOS Core. The IP of the firewall is 192.168.1.1 and the administrator user is named “admin”.
Preparations
The certificate file named fullchain.pem created by certbot contains the full chain with three (3) certificates.
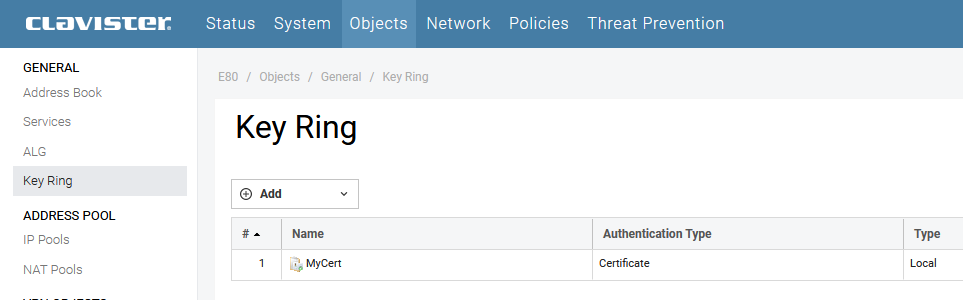
Create three certificate objects under Objects / Key Ring, in this example they will be called MyCert, MyCert_C1 and MyCert_C2.
The first time fullchain.pem needs to be edited (in a text editor), the three certificates split to three files and uploaded to the three separate Key Ring certificate objects (MyCert, MyCert_C1 MyCert_C2). For the domain certificate MyCert the private key from the file privkey.pem also must be uploaded.
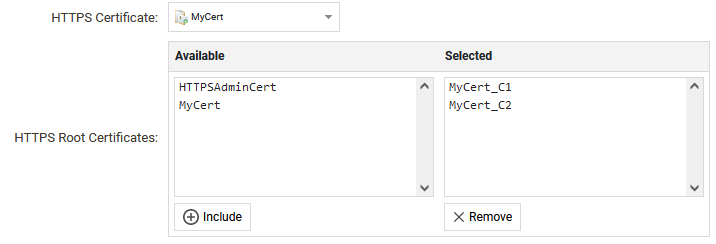
The domain certificate, in this example named MyCert, should then be selected as Certificate in cOS Core (under for example HTTPS Remote Management or IPsec Interfaces) and the other two, in this example called MyCert_C1 and MyCert_C2, as Root Certificates.
Solution Using SCP and SSH
From the host that handles the renewal of Lets Encrypt certificates, issue the following commands or include them in a script that is run periodically.
scp fullchain.pem admin@192.168.1.1:certificate/MyCert
scp privkey.pem admin@192.168.1.1:certificate/MyCert
This will upload the certificate file and the private key under the node named MyCert (which must already exist). After the ssh commands the configuration will be changed, but will not be activated and committed.
To also activate the configuration, use ssh:
ssh admin@192.168.1.1 commit
sleep 5
ssh admin@192.168.1.1 activate


Solution Using cOS Core Built-in Lets Encrypt Handling
As of version 14.00.12 its possible to let cOS Core handle Lets Encrypt certificate updates. See the ACME section in the Admin Guide for more information.
Nginx and Certbot
Nginx: Nginx is a widely-used web server and reverse proxy server. It serves as an intermediary between clients and web servers, managing web traffic.
Certbot: Certbot is an open-source software tool designed to automate the setup and management of SSL/TLS certificates for web servers. It simplifies the process of obtaining and renewing certificates.
Related articles
10 Mar, 2023 core vpn ikev2 windows radius certificate
9 Apr, 2025 core acme letsencrypt
18 Mar, 2024 core certificate oneconnect ipsec vpn
2 Feb, 2021 core sslvpn macos certificate
21 Feb, 2023 ipsec certificate windows ca core
18 Mar, 2024 core incontrol certificate oneconnect ipsec vpn
18 Mar, 2024 onetouch sslvpn oneconnect troubleshoot certificate
14 Mar, 2023 core ipsec vpn ikev2 certificate
11 May, 2023 oneconnect certificate howto
22 May, 2024 netwall ikev2 windows certificate vpn core