Problem Background
The currently recommended certificate chain as presented to Let’s Encrypt ACME clients when new certificates are issued contains an intermediate certificate (ISRG Root X1) that is signed by an old DST Root CA X3 certificate that expires on 2021-09-30. In some cases the OpenSSL 1.0.2 version will regard the certificates issued by the Let’s Encrypt CA as having an expired trust chain.
See more information about the currently issued trust chains at Let’s Encrypt.
In normal cases, Netwall users upload both the actual ‘end certificate’ and ‘root certificate’ to the NetWall firewall. In case the certificate were issued by Lets Encrypt, OneConnect client can show following error when trying to connect to the NetWall:
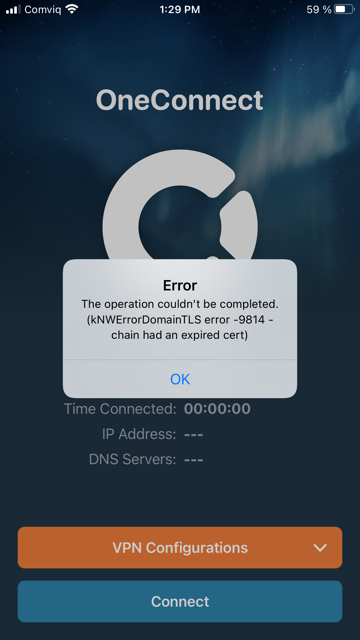
Solution
To overcome above certificate error message, follow the steps below:
Lets Encrypt certificate preparation
- Make sure that the issued certificate is using the alternate lets encrypt chain - "End-entity certificate ← R3 ← ISRG Root X1"
- Create a separate certificate files for all Lets Encrypt root, intermediate and actual certificate to be used by NetWall
NetWall configuration
- Under NetWall's "Objects" -> "Key Ring":
- Add 'Certificate' Object for actual Lets Encrypt certificate file (make sure to upload the private key as well)
- Add 'Certificate' Object for intermediate Lets Encrypt certificate file
- Add 'Certificate' Object for root Lets Encrypt certificate file
- Under NetWall's "Remote Management Settings" -> "Advance Settings":
- Select the actual certificate for the "HTTPS Certificate" setting
- Select and add both the intermediate and root certificates for the "HTTPS Root Certificates:" setting
- Save and Activate NetWall configuration
Related articles
https://www.openssl.org/blog/blog/2021/09/13/LetsEncryptRootCertExpire/
https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/
13 Jun, 2022 oneconnect macos ios windows android
3 Jun, 2022 oneconnect openconnect sslvpn
8 Feb, 2026 oneconnect sase cloud
8 Feb, 2026 oneconnect sase
28 Apr, 2023 openconnect oneconnect macos ios iphone
18 Mar, 2024 core certificate oneconnect ipsec vpn
6 Dec, 2025 sase cloud oidc oneconnect core
28 Feb, 2024 oneconnect windows
23 Aug, 2022 sslvpn openconnect oneconnect android core
29 Oct, 2021 sslvpn openconnect oneconnect windows
9 Feb, 2024 core oneconnect windows splittunneling dns
18 Mar, 2024 core incontrol certificate oneconnect ipsec vpn
27 Oct, 2022 oneconnect log
5 Mar, 2021 sslvpn openconnect oneconnect linux core
8 Apr, 2021 core sslvpn oneconnect interfaces arp
4 Jul, 2025 core oneconnect oidc
18 Mar, 2024 onetouch sslvpn oneconnect troubleshoot certificate
25 Feb, 2022 oneconnect windows howto
8 Feb, 2026 sase oneconnect core userauth oidc
27 Feb, 2024 oneconnect userbased core
23 Aug, 2022 core oneconnect
28 Nov, 2022 core configuration oneconnect
21 Nov, 2025 oneconnect sase cloud radius
29 Jun, 2021 core oneconnect
11 May, 2023 oneconnect certificate howto
27 Aug, 2024 oneconnect windows
8 Jun, 2022 openconnect oneconnect android
23 Aug, 2022 sslvpn openconnect oneconnect macos windows linux core