Question
We want to allow “Path MTU discovery” through a NetWall firewall, how can we accomplish this?
Functionality explanation
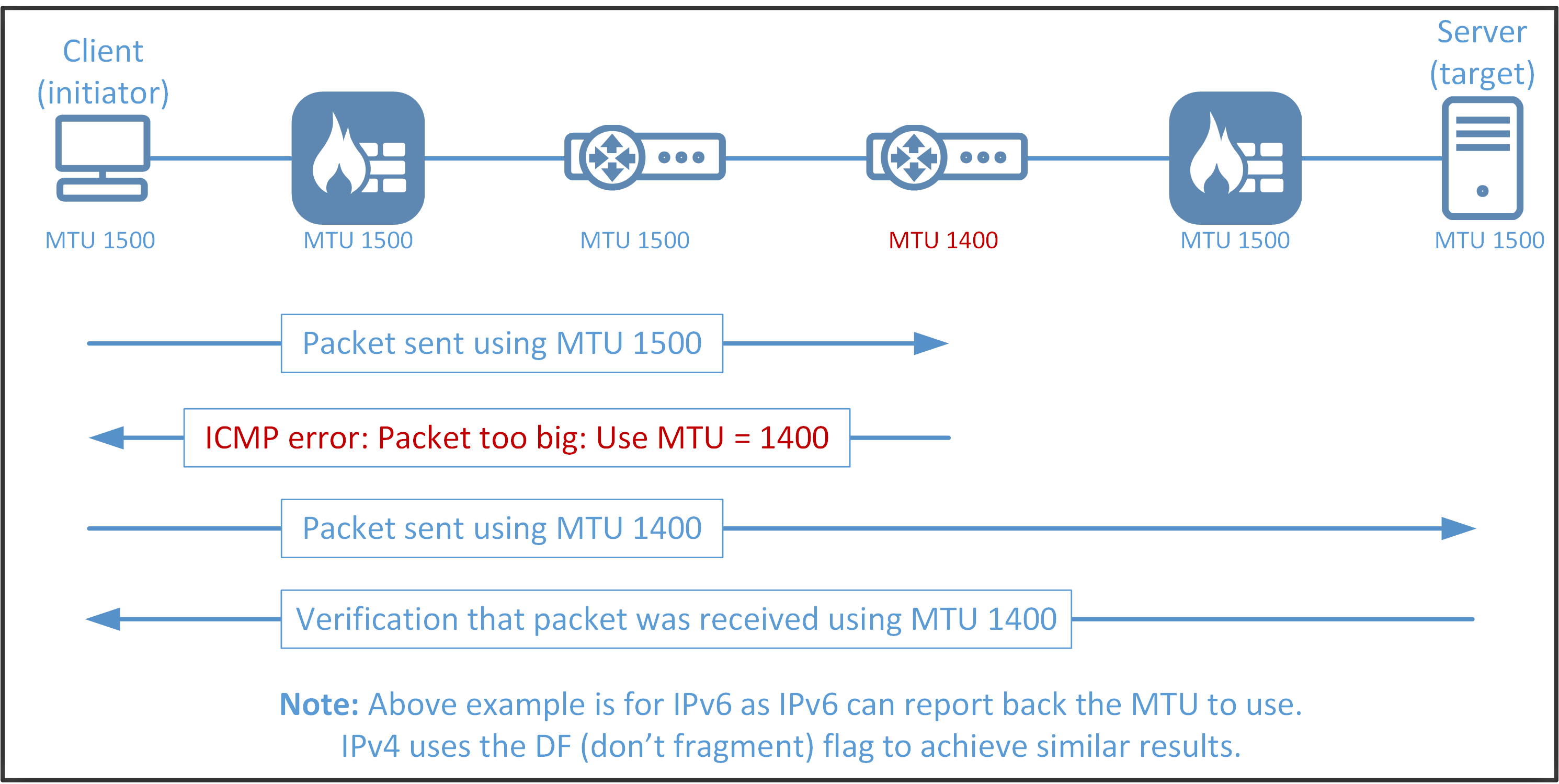
Path MTU Discovery is a standardized technique in computer networking for determining the maximum transmission unit (MTU) size on the network path between two Internet Protocol (IP) hosts, usually with the goal of avoiding IP fragmentation.
For IPv4 packets, Path MTU Discovery works by setting the Don’t Fragment (DF) flag bit in the IP headers of outgoing packets. Then, any device along the path whose MTU is smaller than the packet will drop it, and send back an Internet Control Message Protocol (ICMP) Fragmentation Needed (Type 3, Code 4) message containing its MTU, allowing the source host to reduce its Path MTU appropriately. The process is repeated until the MTU is small enough to traverse the entire path without fragmentation.
For IPv6, Path MTU Discovery works by initially assuming the path MTU is the same as the MTU on the link layer interface where the traffic originates. Then, similar to IPv4, any device along the path whose MTU is smaller than the packet will drop the packet and send back an ICMPv6 Packet Too Big (Type 2) message containing its MTU, allowing the source host to reduce its Path MTU appropriately. The process is repeated until the MTU is small enough to traverse the entire path without fragmentation.
An example of the concept of Path MTU Discovery is visualized in the picture below (IPv6).
Why not allowed by default?
As the NetWall firewall is a network security product we want to avoid letting trace route, ping, or any of the other ICMP messages into and through a network from the Internet, as this would be an invitation for network mapping, and could be the basis for an attack. This is the reason why we do not allow this behavior by default.
How to enable Path MTU Discovery
In cOS Core there are three options that need to be set correctly in order to allow Path MTU discovery.
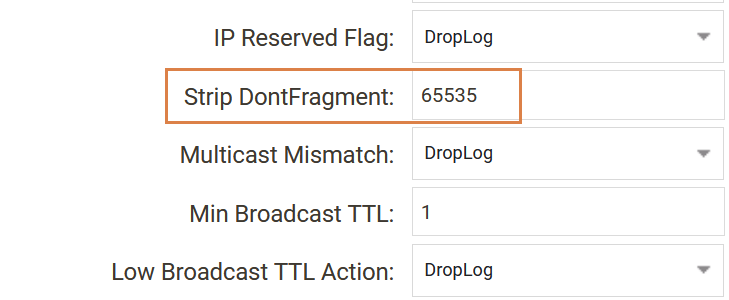
1. “Strip DontFragment”
This setting can be found under System->Advanced Settings->IP in the WebUI. By default, this setting is configured to be 65535 which means that we remove the “Don’t Fragment” flag from all packets. In order to allow Path MTU discovery this needs to be set to a reasonable value where we want to strip the DF flag. In other words, lower than 750.
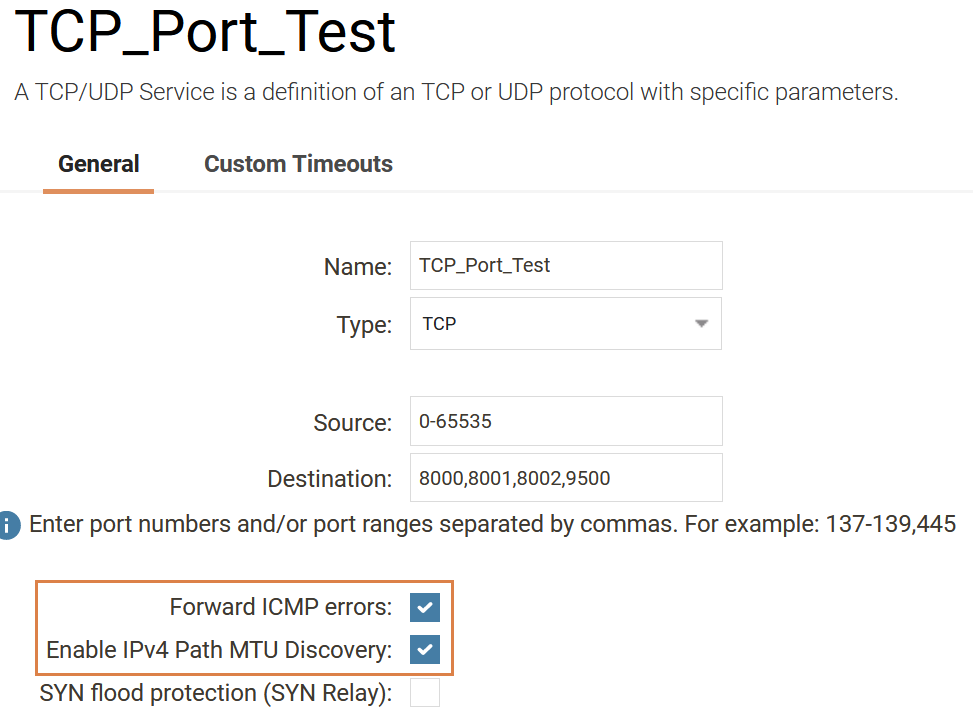
2. “Forward ICMP errors” + “Enable IPv4 Path MTU Discovery”
These settings can be found on all Service objects (Objects->Services). Both settings need to be enabled for each service that will allow Path MTU Discovery.
This topic is described further in the Path MTU Discovery section of the cOS Core Administration Guide.
Additional (optional) information
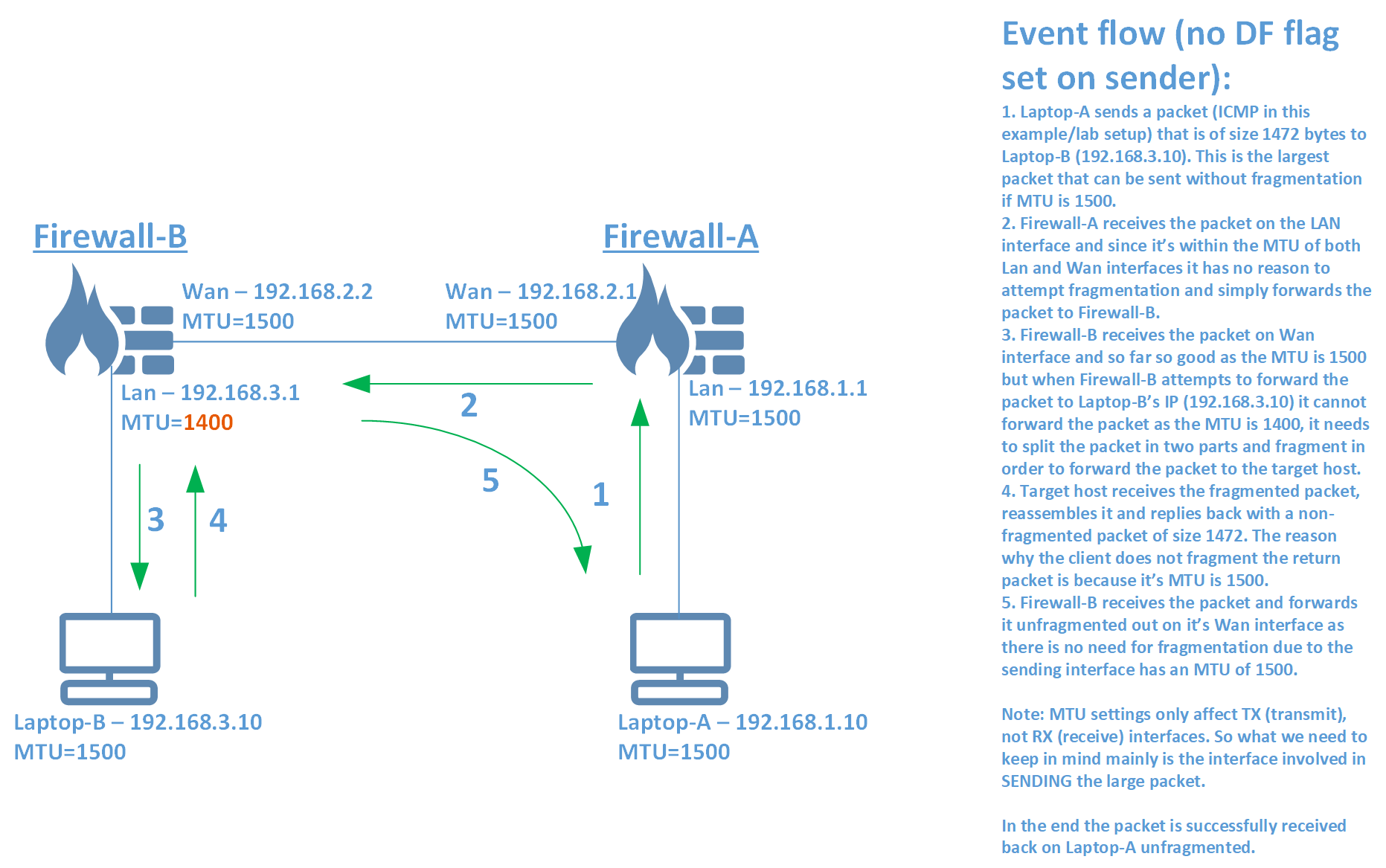
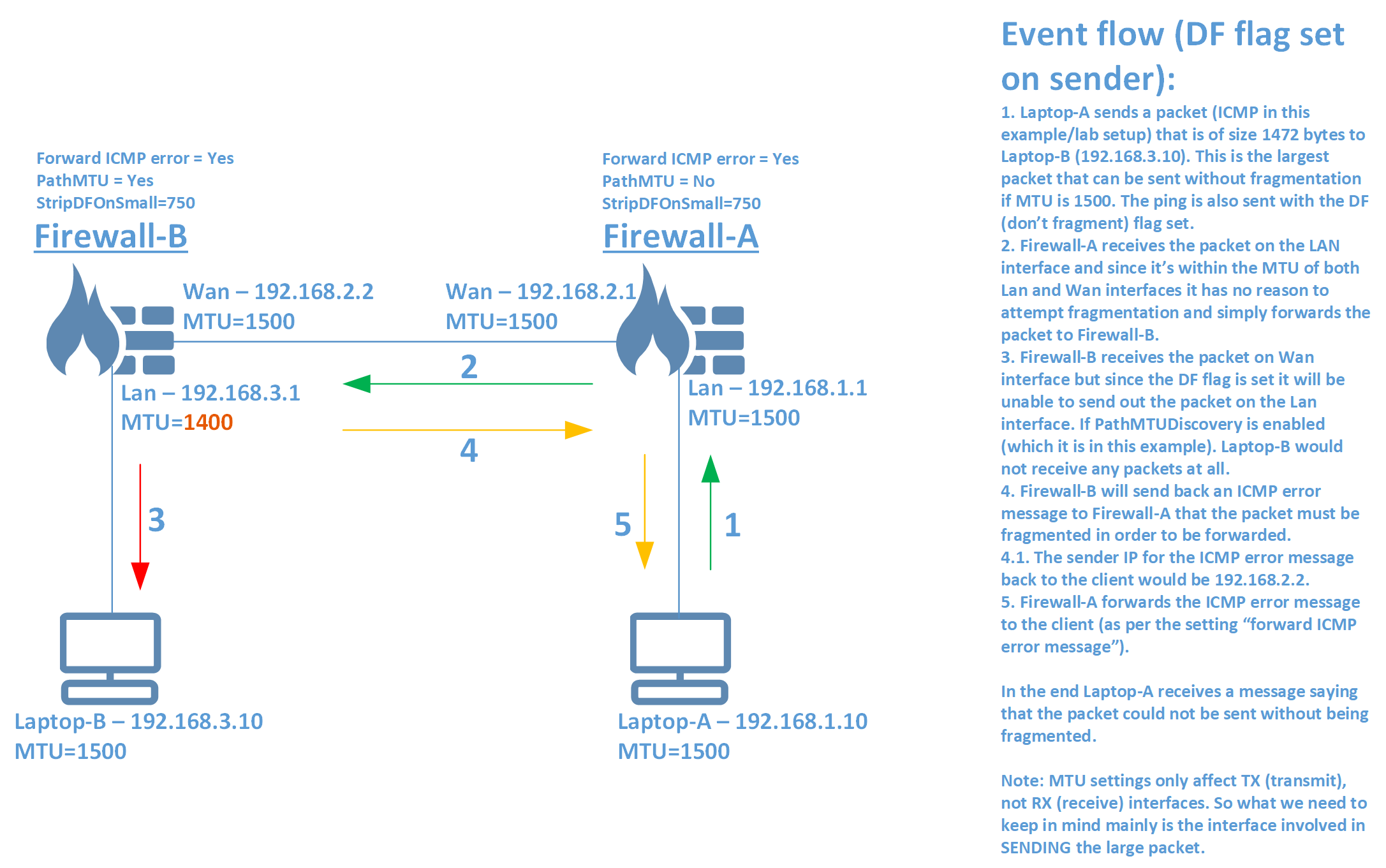
A picture often says more than words and in order to give two examples of an MTU scenario and what happens please see the two pictures below.
Example-1: DF (don’t fragment) flag NOT set on the sender.
Example-2: DF flag set on the sender.
Related articles
No related articles found.