Description
We want to do an automatic translation of the destination port from e.g. port 81 to 80, meaning that whatever destination IP the user connect to using port 81, the port should automatically become 80 when it leaves the Firewall.
Description
This is quite an unusual scenario operation as IP Policies base options do not account for this particular scenario. So we have to configure this quite differently.
An example of how an IP policy should look to solve this scenario is as follows:
Action: Allow
Interface: if2 (or e.g. Lan)
Network: if2_net (or e.g. Lan_net)
Destination Interface: if1 (or e.g. Wan)
Destination Network: 0.0.0.1-255.255.255.255
Service: Destport_81 (TCP Source port 0-65535 & Destination port 81)
Source Translation: NAT
Destination Translation: SAT
Address Action: Transposed
Base IP Address: 0.0.0.1
Port Action: Single port
New Port: 80
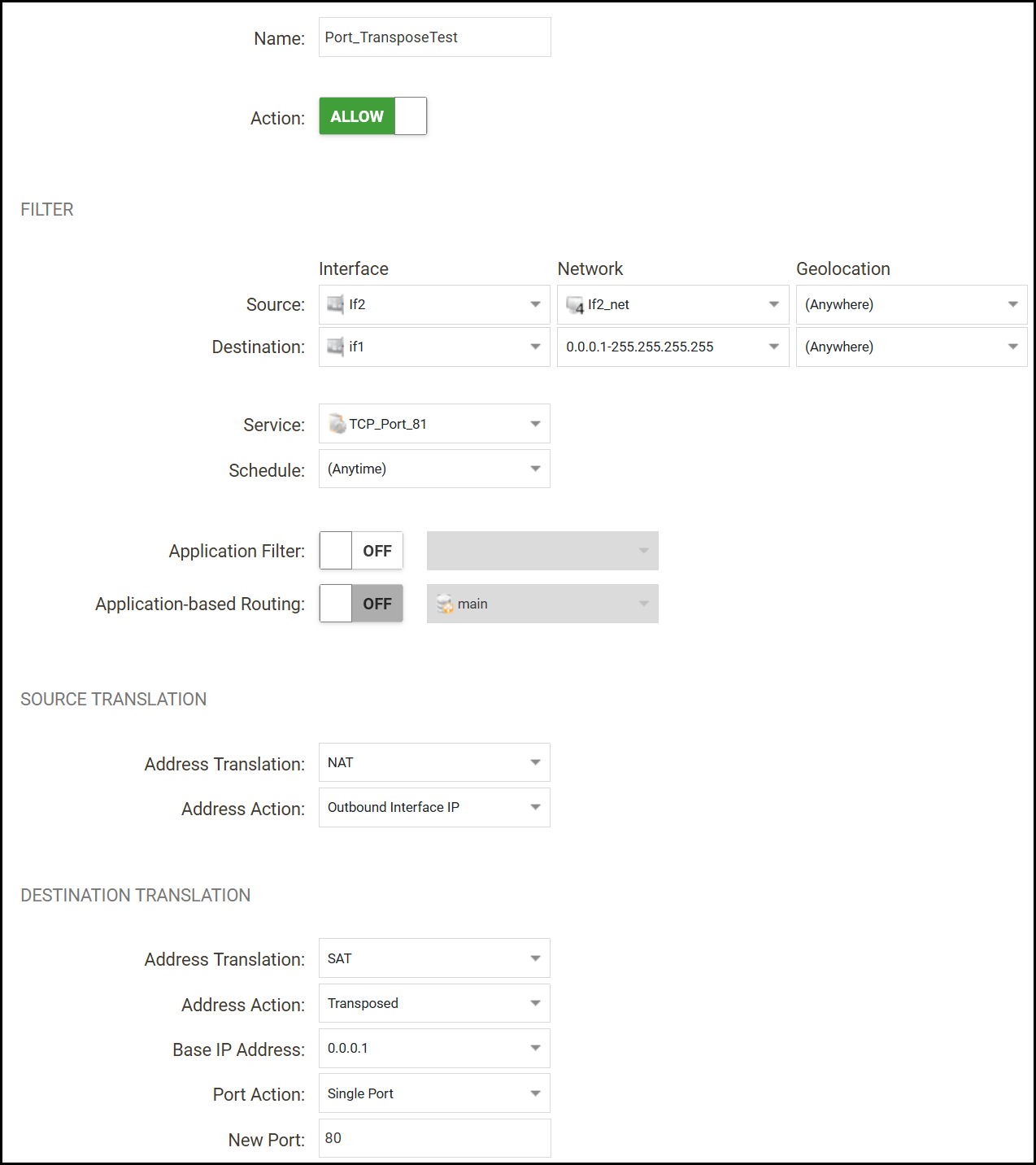
On the SetDest we must also use 0.0.0.1 as that is the first address in the destination network, 0.0.0.0 is invalid and 0.0.0.2 for instance would cause an offset of all destination network addresses by +1.
Note: If we use this setup as the example for HTTP traffic, then we must remember that if we connect to Webpage-A using for instance this syntax:
http://www.test.com:81
It will become 80 when it leaves the Firewall. But the destination webpage most likely links to other HTTP pages using port 80, those will NOT be translated by this rule as it will be a sort of redirection to port 80 that we cannot control. So if we do not have a rule that allows HTTP port 80 in our ruleset, it would cause big delays as the browser is awaiting a reply on port 80 that is blocked by the Firewall.
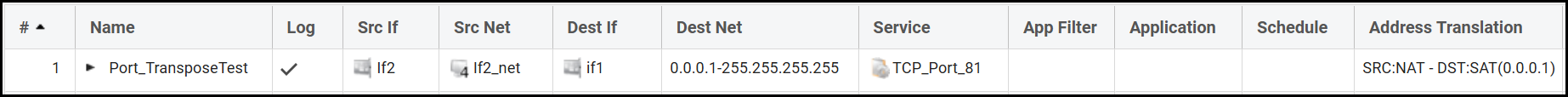
Ping simulation test output
VSG-14:/> ping 1.1.1.1 -srcif=If2 -srcip=192.168.200.50 -tcp -port=81 -verbose
Rule and routing information for ping:
TCP: 192.168.200.50:38557 -> 1.1.1.1:81 allowed by rule "Port_TransposeTest"
Sending 0-byte TCP ping to 1.1.1.1:80 from 192.168.98.14:38557
sent via route "0.0.0.0/0 via if1, gw 192.168.98.1" in PBR table "main"
TCP Reply from 1.1.1.1:81 to 192.168.200.50:38557 seq=0 SYN+ACK time= 10 ms TTL=55
TCP Reply from 1.1.1.1:81 to 192.168.200.50:38557 seq=0 FIN time= 10 ms TTL=55
TCP Ping Results: Sent: 1, RST/ACKs Received:1, Loss: 0%, Avg RTT: 10.0 ms
In the above output we can see that a packet sent to destination port 81 will be changed to be destination port 80 when it leaves the Firewall, so it is working as expected. The response output say that we get a reply from port 81, but that would then be from the “clients” perspective.
Related articles
26 Apr, 2023 core rules
16 Mar, 2023 core incontrol statistics rules
2 May, 2023 core rules schedule applicationcontrol
7 Oct, 2025 core rules
8 Sep, 2020 core ipsec rules access
17 Mar, 2023 core routing rules ping icmp cli