Description
L2TP over IPsec requires an IPsec tunnel that encapsulates the L2TP data when it is transported over an insecure network. This means that the IPsec tunnel will be established first, then the L2TP tunnel will be established inside the IPsec tunnel. This article provides an explanation of how to set up cOS Core to act as a client for an L2TP/IPsec tunnel connection. However, the following points should be noted:
- L2TP/IPsec is no longer recommended for use (since Jan 2023) as many of the default ciphers are now not recommended (such as MD5 and SHA1) and could pose a security risk. Unless the option exists to select and use stronger ciphers, it is recommended to instead use a normal IKEv2 IPsec tunnel. The use of double-encapsulation (L2TP inside an IPsec tunnel) also causes more overhead and only a maximum MTU of 1376 can be used which results in lower performance and potential fragmentation.
- When the L2TP client receives an IP address from the server IP pool, it will cause the cOS Core to initiate a reconfigure (similar to DHCP client).
- If no specific/option setting is mentioned, the default value should be used.
Setting up the IPsec interface
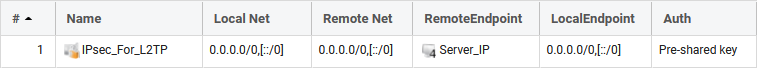
Name: IPsec_For_L2TP
IKE Version: IKEv1 (Important)
Encapsulation Mode: Transport (important)
Remote Endpoint: Server_IP (L2TP/IPsec server IP)
Authentication: PSK or Certificate
IKE and IPsec Algorithms: If possible, we recommend choosing safe proposals such as SHA256 and AES256. (you will need to match the algorithms used by the L2TP Server).
Add Route Dynamically: Disabled
Add Route Statically: Disabled
* *
*
Note: Local Network and Remote Network is not applicable when Transport mode is used. The IPv4 address all-nets (0.0.0.0/0) is not used even though it looks that way visually when examining the IPsec tunnel summary (above).
Setting up the L2TP client interface
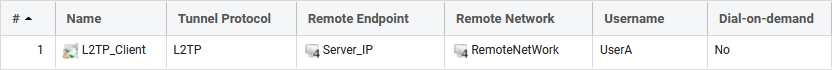
Name: L2TP _Client
Tunnel Protocol: L2TP
Remote Endpoint: Server_IP (same IP/object as used on the IPsec tunnels Remote Endpoint).
Remote Network: RemoteNetWork (this is the network we want to access beyond the L2TP client tunnel).
Authentication: Here we enter the username and password for a user on the L2TP Server.
Under the Security tab: Select the IPsec interface created earlier.
Note: Keep the “Statically Add Route” option enabled
MTU: 1376
IP Policies to allow traffic to and from the network(s) behind the L2TP server
This IP policy allows traffic to be sent to the network(s) behind the L2TP server. If traffic is allowed to be initiated in the other direction, another IP policy for that would be needed.
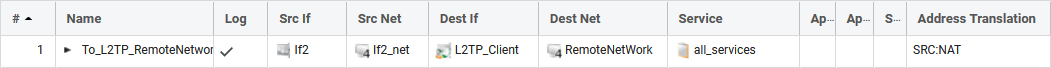
Name: To_L2TP_RemoteNetWork
Action: Allow
Source Interface: If2
Source Network: If2_net
Destination Interface: L2TP_Client
Destination Network: RemoteNetWork
Service: all_services
Note the following:
- Make sure that the destination interface is the L2TP_Client interface and NOT the IPsec tunnel (this is a common setup mistake).
- NAT will most likely be needed (depending on how the server is configured) since the server would most likely not accept incoming traffic from the client's local network range.
Related articles
11 Jan, 2023 ipsec core vpn
24 Mar, 2023 core ipsec ippool dhcp
12 Apr, 2023 core proxyarp arp ipsec routing
18 Mar, 2024 core certificate oneconnect ipsec vpn
23 Nov, 2022 core ipsec
21 Feb, 2023 ipsec certificate windows ca core
22 Mar, 2021 core ipsec routing
18 Mar, 2024 core incontrol certificate oneconnect ipsec vpn
11 Dec, 2025 core routing ospf ipsec
17 Jun, 2021 core ipsec routing
20 Feb, 2023 core vpn ipsec
4 Aug, 2023 core ipsec troubleshoot ike
14 Apr, 2021 core license ipsec
8 Sep, 2020 core ipsec rules access
29 Mar, 2023 ipsec core windows vpn l2tp
5 Apr, 2023 ipsec core
16 Sep, 2020 vpn ipsec ikev2 windows howto dh
7 Dec, 2022 ipsec ike troubleshoot core
14 Dec, 2022 core ipsec
5 Apr, 2023 core nps ipsec radius legacy
14 Mar, 2023 core ipsec vpn ikev2 certificate
23 Aug, 2022 core ipsec license memory
15 Mar, 2023 core ipsec ipv6
23 Aug, 2022 core connections ipsec memory
13 Feb, 2023 ipsec core routing failover
28 Mar, 2023 dhcp ipsec core