Firewall configuration
set RemoteManagement RemoteMgmtSSH RemoteMgmtSSH -enable
Depending on the amount of captured packets and the duration, the SSH setting “SessionIdleTime” may have to be modified in order to avoid the SSH connection timing out. Active packet captures does not count as being active in the SSH session.
set RemoteManagement RemoteMgmtSSH RemoteMgmtSSH SessionIdleTime=<value>
Configure Wireshark
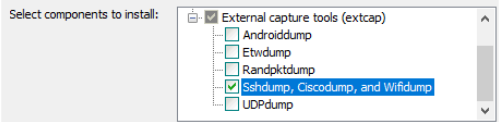
Install component “Sshdump,Ciscodump, and Wifidump” during software installation
Setup connection and filtering 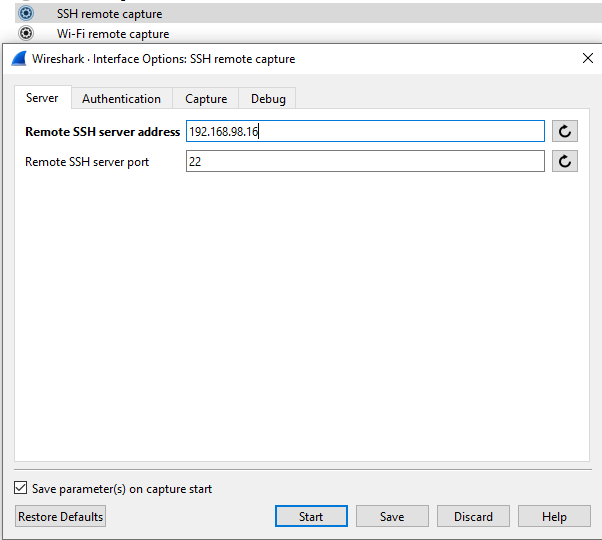
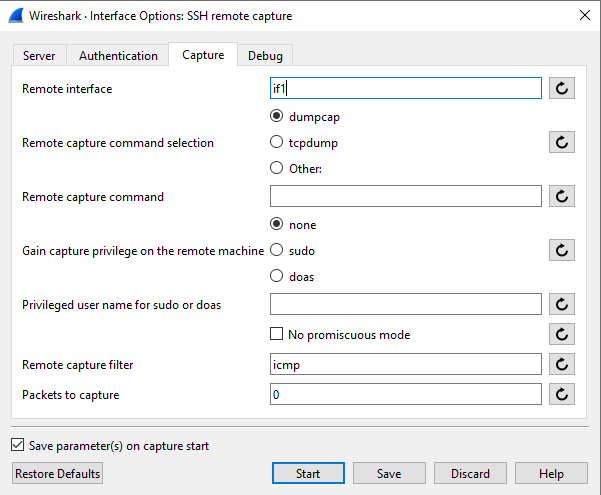
Set remote capture filter, supported and examples below.
Supported IP protocol presets:
TCP / UDP / ICMP / ICMPv6 / IGMP / IPv4 / IPv6 / GRE / ESP / AH / MTP / SCTP / OSPF / L2TP / ip proto <n>
IP filtering keywords:
src host / src net / dst host / dst net / host / net
Ethernet filtering keywords:
ether src / ether dst / ether host
Port filtering keywords:
src port / src portrange / dst port / dst portrange / port / portrange
Filter Examples:
Filter UDP traffic from/to port 53:
udp port 53
Filter OSPF traffic from 192.168.0.1 and 192.168.0.10:
ospf src host 192.168.0.1,192.168.0.10
Filter TCP traffic to 192.168.0.0/16:
tcp dst net 192.168.0.0/16
Filter traffic from/to ports 5000-6000 and 8000-10000:
portrange 5000-6000,8000-10000
Filter traffic from/to ethernet address 00:11:22:33:44:55:
ether host 00:11:22:33:44:55
Filter traffic with IP protocol 100 (GMTP):
ip proto 100
Filter ICMP traffic coming from host 192.168.0.1 going to 192.168.0.2:
icmp and src host 192.168.0.1 and dst host 192.168.0.2
Related articles
27 Mar, 2025 stream proxmox
2 Dec, 2024 core stream tcpsequence sequence stateless
9 Oct, 2025 stream migration
28 Nov, 2022 core stream